The problem, called Bad.Build, lies in the Google Cloud Build service, according to cloud security firm Orca, which discovered and reported the problem.
“By abusing the flaw and enabling impersonation of the default Cloud Build service, attackers could manipulate images in the Google Artifact Registry and inject malicious code,” the company said in a statement shared with The Hacker News. ” ,
“Any application built from the manipulated images is affected and, if the malformed application is to be deployed on a customer’s environment, the risk is shifted from the supply organization’s environment to their customers’ environment, which is a key supply chain.”
Following responsible disclosure, Google has issued a partial fix that does not eliminate the privilege escalation vector, describing it as a low-severity issue. No further customer action is required.
The design flaw stems from the fact that Cloud Build automatically creates a default service account for users to execute builds for a project on behalf of. Specifically, the service account comes with elevated permissions (“Logging.PrivateLogEntries.list”), which allows access to the audit log containing a complete list of all permissions on the project.
“What makes this information so fascinating is that it facilitates lateral movement and privilege escalation in the environment,” said orca researcher Roi Nissimi. “Knowing which GCP accounts can perform which functions is a big part of the puzzle of how to launch an attack.”
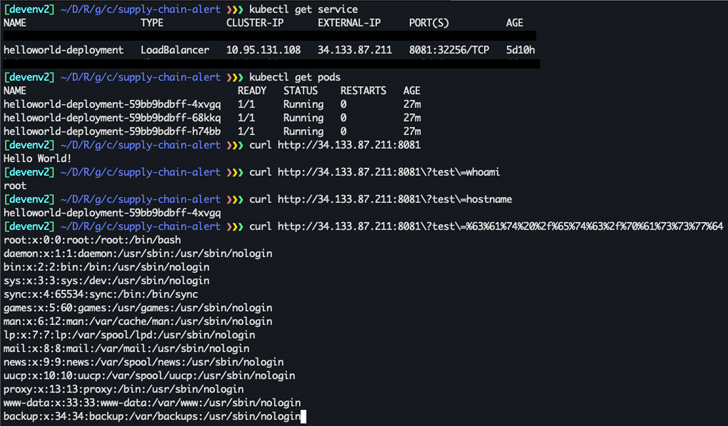
In doing so, a malicious actor could abuse the “cloudbuild.builds.create” permission previously obtained through other means to impersonate a Google Cloud Build service account and gain elevated privileges, inside Google Kubernetes Engine (GKE) Can eject the image in use , and change it to include malware.
“Once a malicious image is deployed, an attacker can exploit it and run code on the Docker container as root,” Nisimi explained.
The patch imposed by Google revokes the logging.privateLogEntries.list permission from the Cloud Build service account, thereby blocking access to enumerate private logs by default.
This is not the first time that a privilege escalation flaw affecting Google Cloud Platform has been reported. In 2020, GitLab, Rhino Security Labs and Praetorian detailed various techniques that can be used to compromise cloud environments.
Customers are advised to monitor the behavior of the default Google Cloud Build service account to detect any potentially malicious behavior as well as apply the principle of least privilege (POLP) to mitigate potential risks.
