Cybersecurity researchers have unmasked a prolific threat actor known as farnetwork, who has been linked to five different ransomware-as-a-service (RaaS) programs over the past four years in various capacities.
Singapore-headquartered Group-IB, which attempted to infiltrate a private RaaS program that uses the Nokoyawa ransomware strain, said it underwent a “job interview” process with the threat actor, learning several valuable insights into their background and role within those RaaS programs.
“Throughout the threat actor’s cybercriminal career, which began in 2019, farnetwork has been involved in several connected ransomware projects, including JSWORM, Nefilim, Karma, and Nemty, as part of which they helped develop ransomware and manage the RaaS programs before launching their own RaaS program based on Nokoyawa ransomware,” Nikolay Kichatov, threat intelligence analyst at Group-IB, said.
The latest disclosure comes about six months after the cyber security company penetrated the Qilin RaaS Gang, which highlights the details of the payment structure of the affiliation and the internal functioning of the RaaS program.
Farnetwork is Known to Operate Under Several Aliases Such as Farnetworkit, Farnetworkl, Jingo, JSWORM, Piparkuka, and Razvrat on Different Underground forums like RAMP Remote Access Trojan Called Referred to as RazvRAT as a Vendor.
In 2022, besides shifting focus to nokoyawa, the russian-spekeing individual is said to have launched their own botnet service to provide affiliates with access to Compromise Networks.
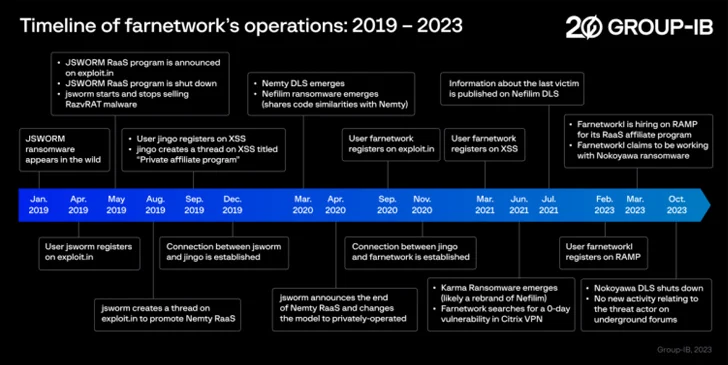
Since the start of the year, farnetwork has been linked to recruitment efforts for the Nokoyawa RaaS program, asking potential candidates to facilitate privilege escalation using stolen corporate account credentials and deploy the ransomware to encrypt a victim’s files, and then demand payment in return for the decryption key.
The credentials are sourced from information stealer logs sold on underground markets, where in other threat actors obtain initial access to target endpoints by distributing off-the-shelf stealer malware like RedLine that are, in turn, pushed through phishing and malvertising campaigns.
The RaaS model allows affiliates to receive 65% of the ransom amount and the botnet owner to receive 20%. The ransomware developer, on the other hand, receives 15% of the total share, a number that could drop further down to 10%.
“From the affiliate’s perspective, this introduces a novel approach as they are not required to get initial access to corporate networks themselves, they can leverage the access that has already been provided by the RaaS manager,” Group-IB’s Threat Intelligence team said.
“While this decreases the percentage of the payout that an affiliate receives, it enhances ransomware operators’ efficiency and speed. Farnetwork’s botnet is used to gain access to corporate networks, effectively replacing the role of initial access brokers.”
Nokoyawa has since ceased its operations as of October 2023, although Group-IB said there is a high probability that farnetwork would resurface under a different name and with a new RaaS program.
“Farnetwork is an experienced and highly skilled threat actor,” Kichatov said, describing the threat actor as one of the “most active players of the RaaS market.”
