The Russia-linked hacking group known as Turla has been spotted using an updated version of a second-stage backdoor called Kazuar.
The new findings come from Palo Alto Networks Unit 42, which has been tracking the rival under its planetarium-themed alias Pensive Ursa.
“As the code of the upgraded revision of Kazuar reveals, the authors put special emphasis on Kazuar’s ability to operate in stealth, evade detection and thwart analysis efforts,” security researchers Daniel Frank and Tom Fakterman said in a technical report.
“They do this by using a variety of advanced anti-analysis techniques and by protecting malware code with effective encryption and obfuscation practices.”
Pensive Ursa, active since at least 2004, is attributed to the Russian Federal Security Service (FSB). Earlier this July, Ukraine’s Computer Emergency Response Team (CERT-UA) implicated threat groups such as DeliveryCheck and Kazuar for backdoor attacks targeting defense sectors in Ukraine and Eastern Europe.
Kazuar is a .NET-based implant that first came to light in 2017 for its abilities to secretly interact with compromised hosts and exfiltrate data. In January 2021, Kaspersky highlighted source code overlap between the malware strain and Sunburst, another backdoor used in conjunction with the 2020 SolarWinds hack.
The improvements to Kazuar indicate that the threat actor behind the operation continues to evolve its attack methods and increase sophistication, while expanding its ability to take control of victims’ systems. This includes the use of strong obfuscation and custom string encryption methods to avoid detection.
“Kazuar operates in a multithreading model, with each core functionality of Kazuar running as its own thread,” the researchers explained.
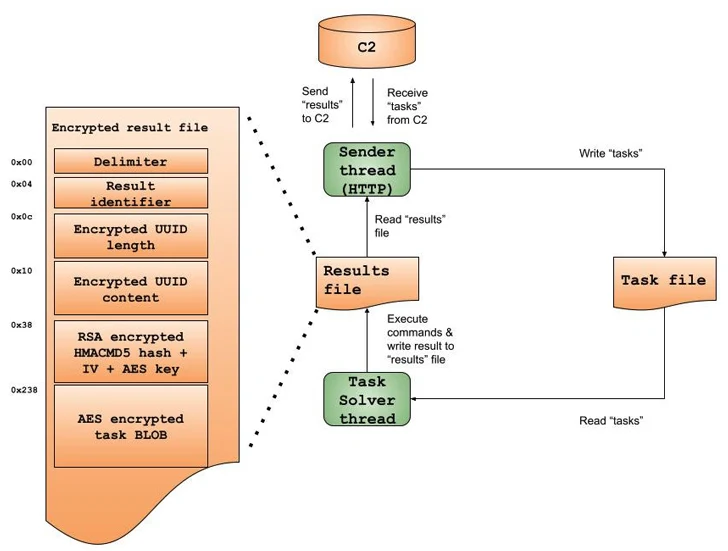
“In other words, one thread handles receiving commands or tasks from its [command-and-control], while a solver thread handles execution of these commands. This multithreading model enables Kazuar’s authors to establish an asynchronous and modular flow control.”
The malware supports a wide range of features – ranging from 26 commands in 2017 to 45 in the latest version – that facilitate extensive system profiling, data collection, credential theft, file manipulation, and arbitrary command execution.
It also includes capabilities to set up automated tasks that will run at specified intervals to gather system data, take screenshots, and grab files from particular folders. Communication with the C2 server occurs over HTTP.
“In addition to direct HTTP communication with C2, Kazuar has the ability to act as a proxy, receiving and sending commands to other Kazuar agents in the infected network,” the researchers said.
“It is doing this proxy communication via named pipes, generating their names based on the machine’s GUID. Kazuar uses these pipes to establish peer-to-peer communication between different Kazuar instances, configuring each as a server or a client.”
Additionally, extensive anti-analysis functionality provides Kazure with a high level of privacy, ensuring that it remains inactive and all C2 communications are turned off if it is being debugged or analyzed.
The development comes as Kaspersky revealed that several state and industrial organizations in Russia were targeted by a custom GO-based backdoor that stole data as part of a spear-phishing campaign that began in June 2023. The threat actor behind the operation is currently unknown.
