High-profile government and telecommunications entities in Asia have been targeted as part of an ongoing campaign since 2021, designed to deploy basic backdoors and loaders to deliver the next phase of malware.
A cybersecurity company called Check Point is tracking the activity under the name Stayin’ Alive. The targets include organizations based in Vietnam, Uzbekistan, Pakistan and Kazakhstan.
“The simple nature of the tools […] and their wide variety suggests they are disposable, mostly used to download and run additional payloads,” a report published Wednesday said. “These tools share no obvious code overlap with products made by any known actors and do not have much similarity to each other.”
What’s notable about the campaign is that the infrastructure shares overlaps with that used by ToddyCat, a China-linked threat actor known for orchestrating cyber assaults against government and military agencies in Europe and Asia since at least December 2020.
Attack chains commence with a spear-phishing email that contains a ZIP file attachment with a legitimate executable that leverages DLL side-loading to load a backdoor called CurKeep by means of a rogue DLL dal_keepalives.dll present within the archive.
CurlKeep is designed to send information about compromised hosts to a remote server, execute commands sent by the server, and write server responses to a file on the system.
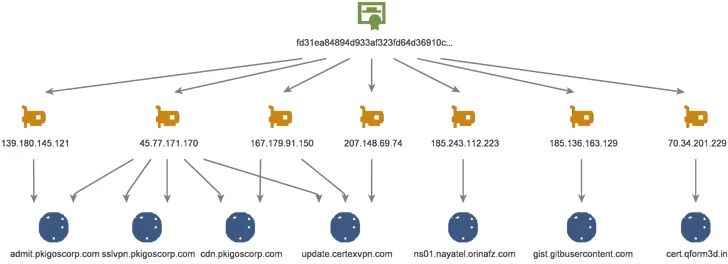
A closer examination of the command-and-control (C2) infrastructure has revealed a constantly evolving arsenal of loader variants dubbed CurLu, CurCore, and CurLog that are capable of receiving DLL files, executing remote commands, and launch a process associated with a newly generated file to which data from the server is written to.
A passive implant called StyleServ has also been discovered that listens on five different ports (60810, 60811, 60812, 60813 and 60814) to accept remote connections and obtain an encrypted configuration file.
Although there is no conclusive evidence linking Stayin’ Alive to ToddyCat, the findings suggest that both intrusion sets use similar infrastructure to go after the same set of targets.
“The use of disposable loaders and downloaders, as seen in this campaign, is becoming common even among sophisticated actors,” Check Point said. “The use of disposable tools makes both detection and attribution efforts more difficult, as they are frequently replaced, and possibly written from scratch.”
