Organizations in the Middle East, Africa, and the Americas have been targeted by an unknown threat actor for distributing a new backdoor called Agent Raccoon.
“This malware family is written using the .NET framework and leverages the domain name service (DNS) protocol to create a covert channel and provide different backdoor functionalities,” Palo Alto Networks Unit 42 researcher Chema Garcia said in a Friday analysis.
Targets of the attacks include various sectors such as education, real estate, retail, non-profits, telecommunications and governments. This activity has not been attributed to any known threat actor, although it is classified as a nation-state threat due to victimization patterns and the use of identity and defense evasion techniques.
The cyber security firm is tracking the cluster under the alias CL-STA-0002. At present it is not clear how these organizations were breached and when the attacks took place.
Some of the other tools deployed by the adversary include a customized version of Mimikatz called Mimilite as well as a new utility called Ntospy, which utilizes a custom DLL module implementing a network provider to steal credentials to a remote server.
“While attackers commonly use Ntospy in affected organizations, the Mimilite tool and Agent Raccoon malware have only been found in the environments of non-profit and government-related organizations,” Garcia explained.
It’s worth pointing out a previously identified threat activity cluster known as CL-STA-0043 has also been linked to the use of Ntospy, with the adversary also targeting two organizations that have been targeted by CL-STA-0002.
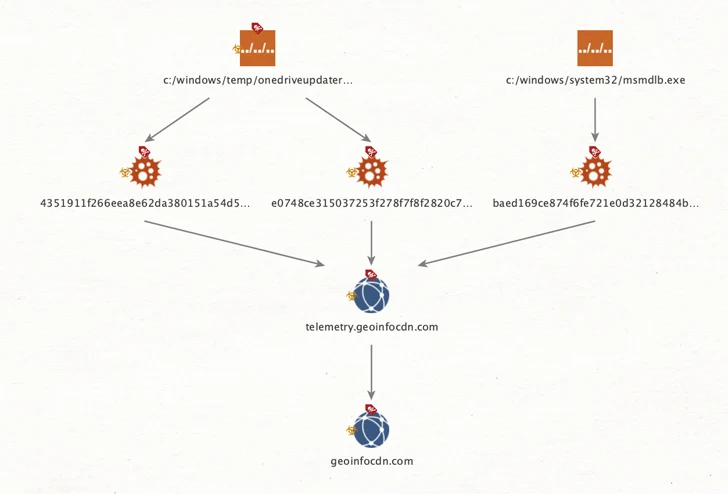
Agent Raccoon, executed through scheduled tasks, allows command execution, file uploading, and file downloading, while disguising itself as Google Update and Microsoft OneDrive updater binaries.
The command-and-control (C2) infrastructure used in connection with the implant dates back to at least August 2020. Examination of the VirusTotal submission of Agent Raccoon artifacts shows that the earliest sample was uploaded in July 2022.
Unit 42 said it also uncovered evidence of successful data exfiltration from a Microsoft Exchange Server environment, resulting in the theft of emails matching various search criteria. The threat actor has also been found hacking the roaming profiles of the victims.
“This tool set is not yet tied to any specific threat actor, and is not entirely limited to a single cluster or campaign,” Garcia said.
