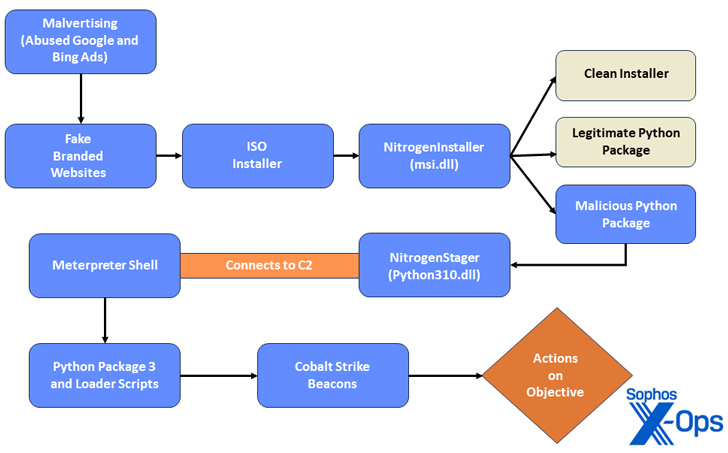
Sophos said in Wednesday’s analysis that the “opportunistic” activity, called Nitrogen, is designed to deploy second-stage attack tools such as Cobalt Strike.
Nitrogen was first documented by Eisentyre in June 2023, detailing an infection chain that redirected users to compromised WordPress sites hosting malicious ISO image files that would eventually execute Python scripts on target systems. Used to execute And Cobalt Strike results in the delivery of the Beacon.
Then earlier this month, Trend Micro revealed a similar attack sequence in which a fraudulent WinSCP application acted as a stepping stone for the BlackCat ransomware attack.
“During the infection chain, threat actors use unusual export forwarding and DLL preloading techniques to disguise their malicious activity and hinder analysis,” said Sophos researchers Gábor Szapanos, Morgan Demboski and Benjamin Solman.
Once launched, the Python script installs a Meterpreter reverse TCP shell, allowing threat actors to remotely execute code on the infected host, as well as a Cobalt Strike beacon to facilitate post-exploitation. Download is allowed.
“Abuse of pay-per-click ads displayed in search engine results has become a popular tactic among malicious actors,” the researchers said. “Threat actors are trying to cast a wide net to lure unsuspecting users looking for some IT utilities.”
The findings also come in the context of an increase in the number of cybercriminals using paid advertisements to lure users to malicious sites and trick them into downloading a variety of malware such as BATLOADER, EugenLoader (also known as FakeBat) and IcedID, which are used to disseminate information thieves and other payloads.
To make matters worse, Sophos said it found “a large number of ads and buzz for SEO poisoning, sales and related services” as well as vendors offering compromised Google Ads accounts on key criminal markets .
This shows that “marketers have a keen interest in SEO toxicity and malware” and “it also downplays the difficulty of bypassing email filters and persuading users to click on a link or download and open an attachment”.
